Malware infections such as SQL injection are a well known security problem. Over the past two years we have seen several large-scale infections on the web, e.g. Gumblar.cn and Martuz.cn. Recently, a new SQL injection campaign called Lizamoon has gained a lot of attention. I had expected web sites would become more secure over time and less susceptible to simple security problems, so it is surprising that SQL injection is still a prevalent problem. That let me to wonder: Was Lizamoon as successful as previous infections? In a discussion about this problem, my colleague Panayiotis Mavrommatis suggested that comparing the size of campaigns via search engine result estimates might not be very accurate measurement.
That begs the question of how to assess the impact of infections. While the number of infected URLs is one possible measure, it is skewed by many different factors, e.g. a single vulnerable site contributes a large fraction of the infected URLs and overstates the impact. Instead, counting the number of infected sites might be a better metric. Even so, to judge the relative scale of an infection campaign, it might be helpful to compare it to previous incidents.
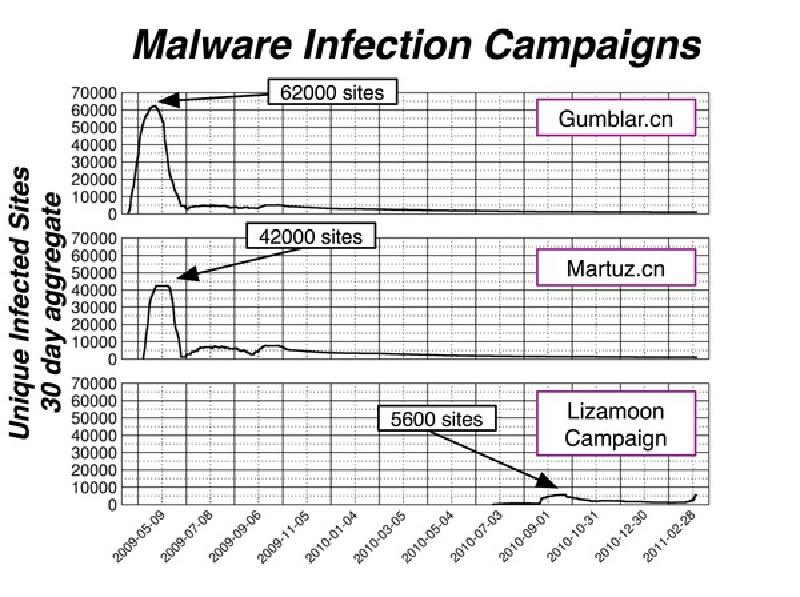
Below is a comparison of the Gumblar.cn/, Martuz.cn/ and Lizamoon infections based on Google’s Safe Browsing data. The graph shows the number of unique infected sites over a 30 day sliding window.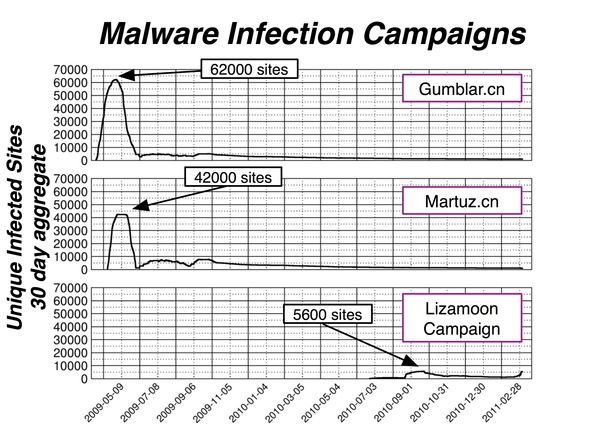
For this analysis, I counted the sites that had a functioning reference to it, e.g. a script src=. Sites that escaped the script tag rendering it harmless were not counted. For Lizamoon, I aggregated the sites provided by the websense blog into a single measure:
hxxp://lizamoon.com/
hxxp://tadygus.com/
hxxp://alexblane.com/
hxxp://alisa-carter.com/
hxxp://online-stats201.info/
hxxp://stats-master111.info/
hxxp://agasi-story.info/
hxxp://general-st.info/
hxxp://extra-service.info/
hxxp://t6ryt56.info/
hxxp://sol-stats.info/
hxxp://google-stats49.info/
hxxp://google-stats45.info/
hxxp://google-stats50.info/
hxxp://stats-master88.info/
hxxp://eva-marine.info/
hxxp://stats-master99.info/
hxxp://worid-of-books.com/
hxxp://google-server43.info/
hxxp://tzv-stats.info/
hxxp://milapop.com/
hxxp://pop-stats.info/
hxxp://star-stats.info/
hxxp://multi-stats.info/
hxxp://google-stats44.info/
hxxp://books-loader.info/
hxxp://google-stats73.info/
hxxp://google-stats47.info/
hxxp://google-stats50.info/
The graph shows two interesting facts.* The Lizamoon campaign started around September 2010 and actually peaked in October 2010 with ~5600 infected sites. At the moment, it seems to be undergoing a revival.
- If we compare the number of infected sites, Gumblar.cn/ is still clearly the winner with ~62,000 sites, followed closely by Martuz.cn/.
For future studies of malware infections, I suggest taking the number of infected sites as a more reliable measure than counting the number of infected URLs.
Update 2011-04-04: The blog post incorrectly referred to Gumblar.cn and Martuz.cn/ as SQL injection attacks. These attacks used stolen FTP credentials.